Amerika.org Under DOS Attack By Scared Leftists
You may have found it difficult to access this site since Friday, May 4, 2018 because an angry group of Leftists have been engaging in a denial-of-service attack against this site and its anti-SJW metal brethren. The bad news is that this took us down intermittently for five days, but the good news is that it shows they fear us.
Leftists realize that 2018 is a huge year because we are fifty years past the Great Revolution of 1968. During that time, Leftist policies have been revealed to (1) fail to fix the problems they claimed were inherent in the old order, and (2) produce even worse problems.
This has caused panic on the Left. They know their time is ending.
In response, they have unleashed an orgy of violence, repression, and censorship — much as history predicted they would do, based on the events in France in the 1700s and Russia in the 1900s — and have attacked what they see as the most accurate voices against them. We are proud to be on that list.
Thank you to all who have written, sent help, bought books, donated time, donated money, and most of all, not given up. They did not break you, and they have not broken us.
Now on to the good details. This DOS attack consisted of two prongs: a TCP/IP-based attack against the machine that hosts several of our sites, and an HTTP-based attack against our PHP-based scripts. Our host, Dreamhost, managed to block the former attack, and with some crufty old 1990s know-how, we have lessened the latter.
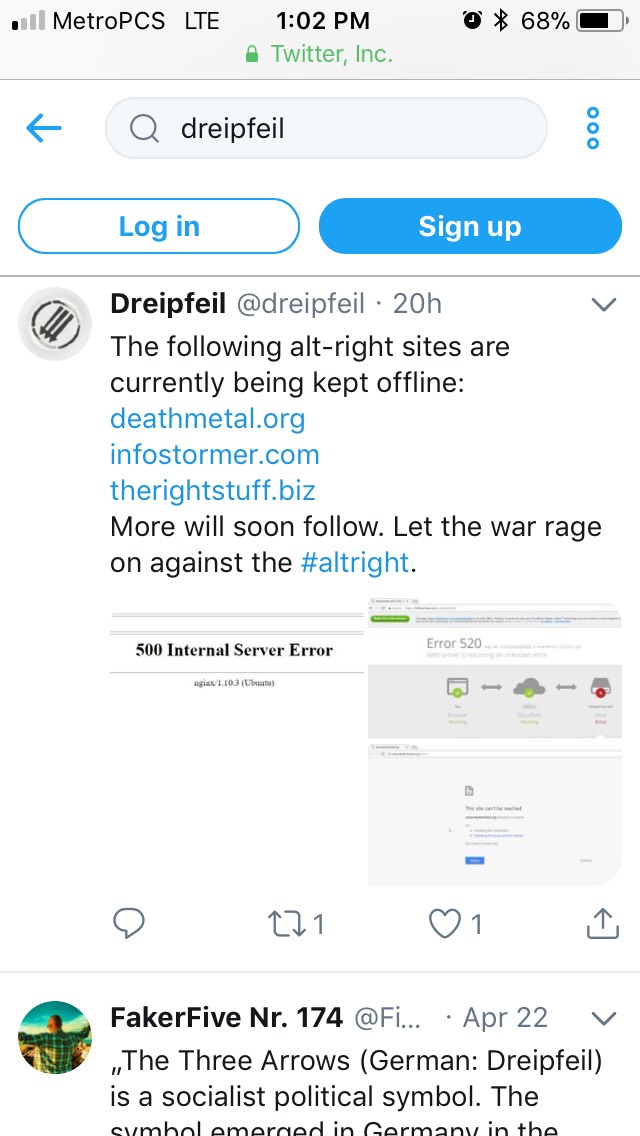
You can see one Leftist crowing about the attack — which also assaulted Gab.ai and American Renaissance, among others — via the Tweet pictured above.
Unfortunately for this Leftist, we have the IP addresses of his friends who are participating in the second prong of the attack. Links go to ARIN which will tell you which ISP owns this address. For the first prong, we think a rented botnet was used, possibly of Russian origin.
156.197.115.103
201.6.241.88
90.86.177.149
50.33.53.90
41.250.212.244
195.55.255.158
41.248.201.66
89.101.246.18
177.11.148.220
146.255.180.237
89.101.246.18
156.197.115.103
109.237.120.70
95.84.65.36
125.59.41.7
186.89.119.5
190.62.35.248
213.87.101.92
177.35.204.164
202.80.214.99
186.92.211.82
89.211.190.40
50.33.53.20
222.124.79.40
5.36.106.166
64.121.90.128
98.204.103.9
172.69.70.153
172.68.27.82
One of these IPs has been linked in the past to one Tulio Baars, who uses the email addresses borrull@eircom.net and tuliobaars@gmail.com, who you can find on Facebook and LinkedIn.
Baars works at Garage and Catarse, where he uses many of the same technologies employed in this attack. We continue investigating. In the meantime, several of the IP addresses used were linked to other email addresses such as 13@hotmail.com, anak1987@gmail.com, and ipmilman@gmail.com. They seem to mostly be active at night, suggesting that they run their scripts and then go off to bed.
We will keep you posted with further announcements. In the meantime, thank you for reading and helping us weather this storm.
Tags: censorship, ddos attack, dos attack, outage, tulio baars